Executive Summary
In a coordinated international initiative, the ASD, CISA, FBI, and their partners released the “Bulletproof Defense” guide. This document goes beyond simple warnings; it provides a technical methodology to dismantle the tactical advantage of Bulletproof Hosting (BPH) providers. These actors are not merely lax hosts; they are architects of cybercrime, providing infrastructure resilient to legal demands. The guide advocates a shift from reactive defense (blocking individual IPs) to proactive volumetric defense (blocking entire Autonomous Systems) and details decision matrices for assessing false positive risks [1].
In-Depth Analysis: The BPH Ecosystem
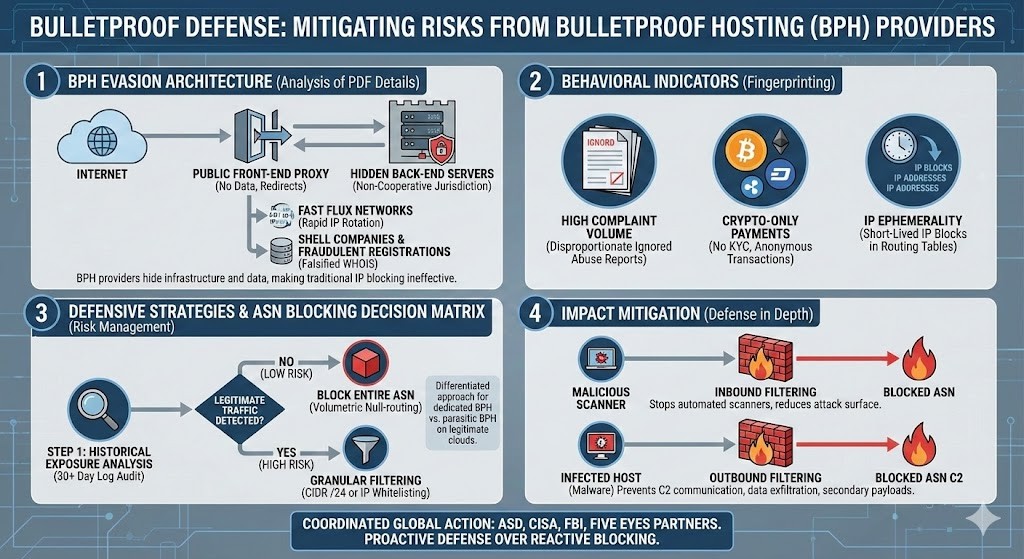
Technical Architecture of Evasion The report details how BPH providers structure their networks to ensure resilience:
- Task Compartmentalization: BPH providers physically separate content hosting servers (often located in jurisdictions with weak cyber laws) from management and payment servers.
- Fast Flux Networks: They utilize botnets or compromised machines to rapidly rotate IP addresses associated with a malicious domain name. A single phishing campaign can resolve to hundreds of different IPs within minutes, rendering IP-by-IP blocking ineffective [2].
- BGP Abuse: BPH providers manipulate the BGP protocol to announce stolen or temporarily leased IP prefixes, vanishing before Regional Internet Registries (RIRs) can take action.
Behavioral Indicators (Fingerprinting) To identify a BPH without relying solely on threat lists, monitors should look for these characteristics:
- Complaint Volume: A disproportionate ratio of ignored abuse reports relative to the total number of hosted IPs.
- Payment Methods: Exclusive acceptance of cryptocurrencies or unregulated digital currencies, with no credit card payment options (which require KYC).
- IP Ephemerality: IP blocks that appear and disappear from global routing tables on very short cycles (days or weeks) [3].
Advanced Defense Strategies and Risk Management
1. Blocking at the Autonomous System (ASN) Level This is the central and most aggressive recommendation. Rather than chasing thousands of IPs, defenders must block the entire ASN (the network identification number of the provider).
- Assessment Methodology: Before blocking ASN X, the defender must consult their logs (SIEM) over 30 to 90 days. If no legitimate communication has occurred with this ASN, the blocking risk is deemed low.
- Handling False Positives: If the ASN hosts both malicious and legitimate services (in cases where BPH providers resell space on known clouds), total blocking is impossible. Defenders must then revert to filtering by subnets (CIDR /24) [2].
2. Defense in Depth: Inbound vs. Outbound
- Inbound Traffic: Preemptive blocking of BPH ASNs reduces the attack surface by stopping automated scanners looking for unpatched vulnerabilities dead in their tracks. This reduces noise in security logs, allowing analysts to focus on subtler threats.
- Outbound Traffic: This is the critical measure to limit the impact of a successful infection. If malware attempts to contact its Command and Control (C2) server hosted on a blocked BPH, the communication fails, preventing the download of secondary payloads (such as ransomware) or data exfiltration [1].
3. ISP and Transit Responsibility The document calls on transit providers (Tier 1 and Tier 2) to stop routing BPH traffic. ISPs must implement strict BGP filters (RPKI) to prevent BPH providers from hijacking routes or announcing IP spaces they do not legitimately own [3].
Sources
- (1) Cyber.gov.au (ASD): https://www.cyber.gov.au/about-us/view-all-content/news/new-guidance-for-mitigating-risks-from-bulletproof-hosting-providers
- (2) CISA (Main Page): https://www.cisa.gov/resources-tools/resources/bulletproof-defense-mitigating-risks-bulletproof-hosting-providers
- (3) Joint Cybersecurity Advisory (Full PDF): https://www.cisa.gov/sites/default/files/2024-10/Guide-to-Mitigating-Risks-from-Bulletproof-Hosting-Providers.pdf



