Access Control Execsum
This is my tips about CISSP preparation. Access Control is at the heart of information security. for that matter, access control is at the heart of all security. The CISSP candidate must fully understand access control concepts (including control types and authentification, authorization and accounting), system access controls (including identification and authentification techniques, methodologies and implementation, and methods of attack), and data access controls (including access control techniques and models) within centralized and decentralized computing environnements.
Basic Concept of Access Control
Access Control, in the context of information security, permits an organization’s management to define and control which systems or ressources a user has access, to and what that user ca do on that system or ressource. More formally, access control is the ability to permit or deny the use of an object (A passive entity, such as a system or file) by a subject. (An active entity, such as an individual or process). Such use is normally defined through sets of rules or permissions (such as Read, Write, Execute, List, Change and Delete) and combinations of various security mechanisms (such administrative, technical and physical control).
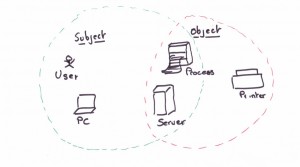
Remember: A subject is an activity entity (Individual or process) that accesses or acts upon or accesses.
Control Types and purposes
You achieve access control through an entire set of controls which, identified by purpose, include:
- Preventive Controls, for reducing the risk
- Detective Controls, for identifying violation and incidents
- Corrective control, for remedying violation and incidents and improving existing preventive and detective controls.
- Deterrent controls, for discouraging violations
- Recovery controls, for restoring systems and information
- Compensating control, for providing alternative ways of achieving a task
You implement most access control mechanisms with the primary goal of reducing risk. Detective, corrective,deterrent, recovery, and compensating controls work in complementary manner with preventive controls to help create an organizations’s overall security posture.
Access controls can be administrative, technical, or physical.
Administrative Controls
Administrative controls include the policies and procedures that an organization implements as part of overall information security strategy. Administrative Controls ensure that technical and physical controls are understood and properly implemented in accordance with the organization’s security policy (PSSI en Français). The purpose of administrative controls is most often preventive and detective, although you can also implement them as deterrent and compensating controls. Administrative controls may include:
- Policies, standards, guidelines, and procedures
- Security Awareness training
- Asset classification and control
- Employment policies and personnel practices (background check, job rotation, and separation of duties and responsibilities).
- Account administration
- Account, log, and journal monitoring
- Review of Audit trails
Technical Controls
Technical (or logical) controls use hardware and software technology to implement access control. Dont’ forget on CISSP exam use both terms.
Preventive technical control include:
- Encryption: Data Encryption Standard (DES), Advanced Encryption Standard (AES) and Merkle-Hellman Knapsack (non pas angela merkel…)
- Access Control Mechanism: Biometrics, Smart Cards, and tokens
- Access Control List: Permission lists that define what a subject can or cannot do to an object.
- Remote access authentication protocols: Password Authentication Protocol (PAP), Challenge Handshake Authentication Protocol (CHAP), Remote Authentication Dial-In User Service (RADIUS), and Lightweight Directory Access Protocol (LDAP).
Detective technical control include:
- Violation reports
- Audit trails
- Network Monitoring and Intrusion Detection
Physical Controls
Physical Controls ensure the safety and security of the physical environnement. There are primarily preventive or detective in nature.
Preventive physical controls include:
- Security Perimeters, such as fences, locked doors, and restricted areas
- Guards and dogs
Detective Physical controls include
- Motion detectors
- Video cameras
- …
Access Control Services
Access control systems provide three essential services
- Authentication
- Authorization
- Accountability
Authentication
Authentication determines wheter a subject can log in.
Authorization
Authorizaton (also referred to as entablishment) defines the rights and permissions granted to a user account or process (What you can do). After a system authenticates a user, authorization determines what that user can do with a system or ressource. Authorization (or etablishement) determines what a subject can do (as defined by assigned rights and permissions).
Accoutability
Accoutability determines what a subject did.
Categories of Access Control
The two categories of access controls are
- System Access Controls: Controls in this category protect the entire system and provide a first line of defense for the data contained on the system.
- Data Access Controls: Controls in this category are specifically implemented to protect the data contained on the system.
Identification and Authentication
Identification is the act of claiming a specific identity. Authentication is the act of verifying that identity.
Password and passphrases
A passphrase is a variation on a password; it user a sequence of characters or words, rather than a single password. Generally, attackers have more difficulty breaking passwphrase than breaking regular passwords because longer passphrases are genarilly more difficult to break than complex passwords.
You can use a software tool that helps users evaluate the quality of their passwords when they create them. These tools are commonly know as password/Passphrase generators or password appraisers.
Personal Identification Number (PINs)
A PIN in itself is a relativity weak authentication because you have only 10.000 possible combinaisons for a four digit numeric PIN.



